The insider threat has evolved beyond the reach of employee bag checks and point-of-sale cameras. For all organizations, retailers included, the threat surface that employees can attack has grown, and so have the types of assets that they can exploit, misuse, or mistakenly expose. Never has so much of value been this accessible to a company’s workforce. Never have companies been so vulnerable to their dishonesty, mistakes, or retribution.
Below are quotes compiled from interviews with security consultants, technology officers, LP executives, and expert presenters at the 2020 ISC and GSX+ conferences. To read an in-depth article about insider threats, see “Our Own Worst Enemy?”
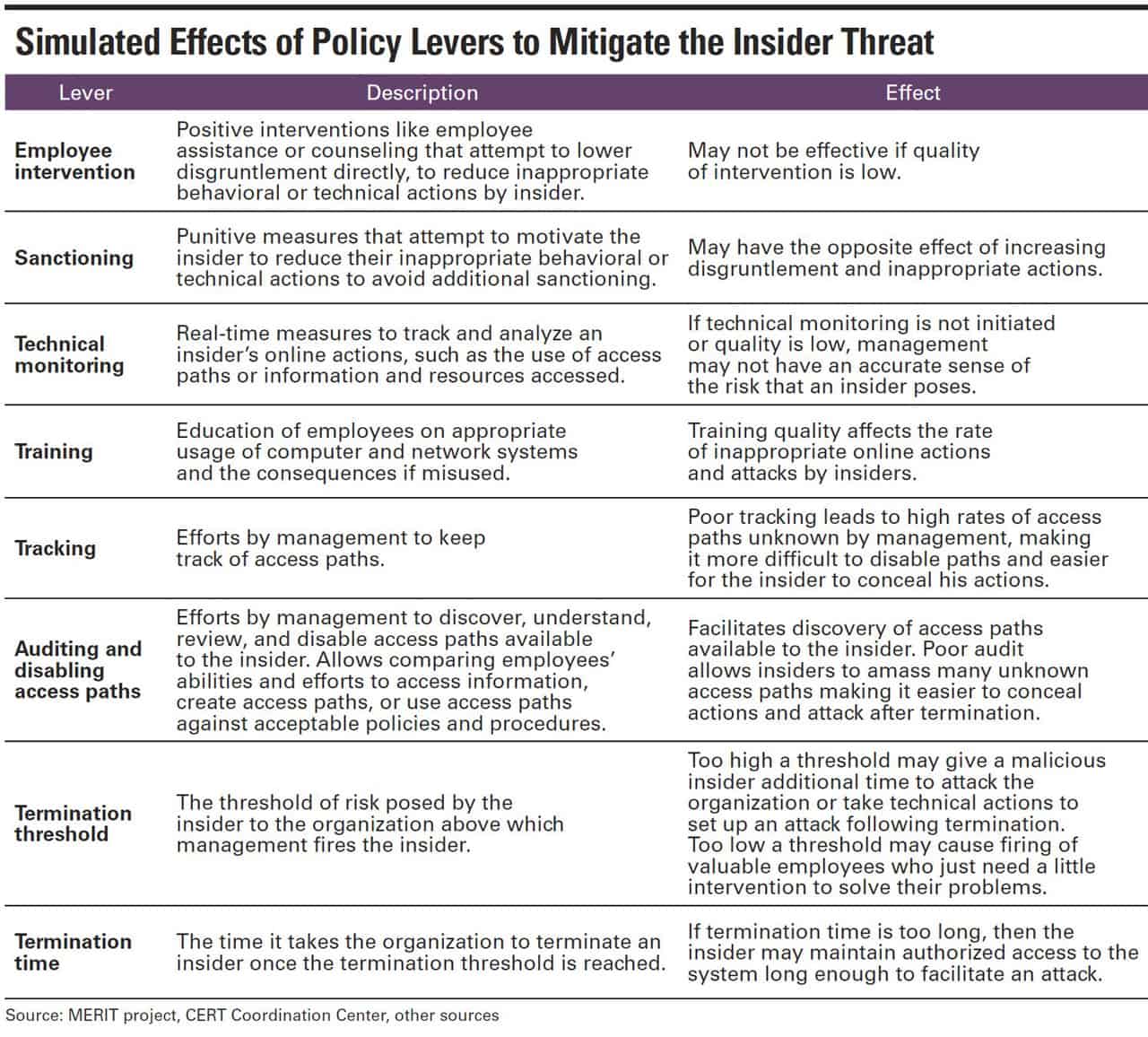
- A governance model is a key foundation of an insider risk program.
- Retailers that segregate systems and are compliant with all required data security and privacy safeguards already greatly reduce insider risk, but you need to be compliant and auditing.
- Use tabletop exercises to examine how your organization would respond to different changes in employee behavior and in a range of different insider threat events.
- Educate senior people about insider threats to prevent an overly “trusting” attitude to flow from the top down.
- To avoid a conflict of interest, incidents captured by an employee hotline or “ethics line” should be accessible by more than one department: HR, legal, security, internal audit, or others.
- Create an insider incident response plan.
- Review controls for time and attendance fraud: it is both exceedingly common and more costly to organizations than most realize.
- Whenever you hire a contractor or consultant, you need to confirm that the individual is not a former employee who was fired for cause.
- Business partner access to computer networks should be accompanied by a formal permission request and an internal business case for why network access is needed.
- Any manager who supervises tech workers that can sabotage company systems should be trained on relevant risk markers, including emotional outbursts, black-and-white thinking, inability to take constructive criticism, and disengagement.
- Social media is an excellent early warning source of potential insider threat activity.
- Insider threat programs can harm morale if operated carelessly. Run all insider threat program activity through a prism of employee privacy and morale issues. Ask, “Does it bring true value to your strategy?”
- Bring a whole-threat approach to an insider threat program.
- Be mindful that money is probably in short supply for company insider risk programs and use that to guide how you advocate for reducing insider threats. A key issue is how you are going to measure and show a return for effort spent to reduce the insider threat.
- Company risk managers are valuable but often underutilized assets for preventing insider threat activity.
- Rotating roles is an excellent practice to ensure redundancy in an organization, improve morale, and deter employee fraud. Separation of duties is an internal business control that helps prevent fraud and identify errors.
- Whether or not you have an established insider threat program, you are probably dealing with insider incidents. It’s important to step back to view how they are being handled and see if there are ways that coordinating the effort might provide efficiencies or reduce risk.
- Including security in new employee orientations can help build a security culture and foster a culture of trust around security issues that makes insider threat activity less likely.
- Top executives can be unintentional insiders. By posting pictures of a family vacation in Spain on Instagram, for example, they create opportunities for spoofing attacks.
- Training the team that is going to be doing an internal investigation is critical. You want to make sure they understand what the process, procedures, and protocols are and that they don’t do their own thing—not only because privacy and employee relations are on the line in insider investigations, but also to avoid overlooking something or missing part of the process.
- Evaluate contracts for whether they prohibit files to be transferred across unprotected networks/systems, which home/personal systems won’t meet.
- Background checks for store employees need to be particularly rigorous for individuals who are going to have access to critical or sensitive data. Especially at middle market retailers, these checks are frequently too cursory.
- Data breach detection, investigation, and response protocols are critical because too often retail organizations have problems detecting and dissecting breaches. It’s why some surveys report external hacking is the source of most incidents while others say it’s insiders.
- Companies allocate resources to protect customer, medical, and payment card information, as they should, but more emphasis needs to be placed on protecting the intellectual property and data that has intrinsic value. If IP is lost, it can cause long-term competitive harm.
- If the issue is solely data leakage, then IT pros can carry the heavy load. But when motives are more sinister, security leaders need to step in.
The article was originally published in November 2020 and updated in August 2021.


