Loss prevention executives are keenly aware of the threat from insiders. After all, we’re many decades removed from when industry data revealed that employees—not shoplifters—were a greater cause of shrink. We’ve set up delivery controls, auditing systems, and background check protocols. We create exception reports to bubble-up workers associated with anomalous transactions. We zoom in on cashiers who issue an inordinate number of discounts to see if they’re pocketing proceeds. We do trust, but we are big on verify.
The insider threat, however, has evolved beyond the reach of employee bag checks and point-of-sale (POS) cameras. For all organizations, retailers included, the threat surface that employees can attack has grown, and so have the types of assets that they can exploit, misuse, or mistakenly expose. Never has so much of value been this accessible to a company’s workforce. Never have companies been so vulnerable to their dishonesty, mistakes, or retribution.

“There are threats posed by insiders at retail organizations that go unaddressed,” warned Florindo Gallicchio, managing director at NetSPI, a penetration testing firm out of Minneapolis. “Oftentimes, only the most obvious threats are considered, such as stealing money from the cash drawer,” he told LP Magazine.
The insider problem is not particularly acute in retail, but it is not less serious, according to Mario Paez, director of cyber and technology errors and omissions at Marsh & McLennan Agency. From his vantage point—dealing with incidents handled by insurance companies—he is witness to events and the full range of potential harms.

“In the retail environment, we certainly are seeing issues like in any other organization,” he said. “You might have line-level employees who gain access to a corporate database through an in-store network; vendors and supply chain providers that might have access to your sensitive information; a rogue employee in the IT department with unchecked access; and intellectual property available to numerous employees in different functions in retail organizations.”
The volume of transactional data that the retail industry produces is second to none, but there is more than customers’ payment information. There are marketing plans, and contracts, and financial reports, and strategy papers, and legal agreements, and store and distribution center blueprints, and much more.
So what should retailers do about today’s exposure? A theme emerges after listening to experts speak on the insider threat. Just as the insider threat has broadened, retail organizations may need to broaden their perception and management of the insider threat to stay ahead of it.
One Problem, Many Avenues
The annual GSX+ security conference was forced to go virtual in September, so it was no surprise that discussions of the pandemic dominated the event. How security professionals can navigate the risks it has catalyzed, the way it has reshaped the threat environment, and how organizations can build resilience against future seismic events were all frequent points of discussion. But while the pandemic was an ever-present backdrop, specific security topics were also in focus—and none more so than the insider threat. Discussions on the harm that employees and other trusted parties can do dominated the proceedings.
The frequency of events is undoubtedly one force driving attention. A significant majority of organizations, 70 percent, say they’ve suffered an increase in insider attacks over the last twelve months, according to Haystax’s Insider Threat Report. Insiders pose the biggest cyber-security problem because they can cause the most damage and are harder to detect and prevent, say experts.
The expanding threat surface is surely another. Trade secrets, innovation, brand reputation, intellectual property—these now tend to be an organization’s most vital assets, not just for technology companies but also in manufacturing, services, and even industries like retail. The effectiveness of corporate security today depends significantly on how well organizations manage this shift from securing hard assets to protecting intangible aspects of company value. “It’s easier to be mindful of insiders related to technology and the payment process, but it goes beyond that to all sensitive information that needs safeguarding,” said Paez. It is within context of the dishonest worker that companies have an opportunity to improve both the protection of customer data and trade secrets/proprietary information, say experts. The same protective measures that retail organizations should adopt to guard the privacy of customer data can safeguard companies’ own secrets as well.
Speed is another complicating factor. In today’s warp-speed business cycle, there is less time than ever to mull over the possible security implications of every business move. Companies must change, adapt, and dive into new opportunities just to stay alive, including embracing new communications technologies. At the same time, companies are engaging in a greater exchange of information with more constituencies to drive innovation and become more efficient. Sharing and integrating information across the global retail enterprise—and with customers, partners, and suppliers—is seen as critical to survival. “As more processes are performed by suppliers, the integrity of those suppliers is becoming ever more important,” warned Paez.
Consider the wide range of insiders that organizations think pose significant security risk, according to the Haystack survey: privileged IT users/administrators, 59 percent; contractors/service providers/temporary workers, 52 percent; privileged business users, 49 percent; regular employees, 49 percent; other IT staff, 25 percent; executive managers, 24 percent; business partners, 16 percent; and customers/clients, 15 percent.
An independent study by Ponemon Institute, sponsored by IBM, examined actual insider-related data breach events impacting organizational costs over the past twelve months. Financial firms were the greatest victims. Retailers landed near the middle of the thirteen industry sectors examined, suffering less than hospitality companies but more than consumer products firms. But while some other industries may lose more, the amount lost by the retailers in the survey was not significantly less than the annualized total losses suffered by firms in the most affected industries.
Generally, the insider threat seems well appreciated, but data show organizations are paying a growing price for them. Why? Paez thinks there is a need for companies to address the risk more comprehensively. It can be strictly seen as a chief information security officer function, or as a security systems technology issue, but success relies on a wide range of activities by many players, starting with whom the retail organization employs. “It is important to understand the integrity and character of the people being hired. HR should be involved on the hiring front and for handling the disciplinary process,” said Paez.
Because of the diffuse nature of the threat, Paez said that the organizations he sees managing the insider threat most effectively typically address it with a committee rather than making it the responsibility of a single function. He said it’s important to have a realistic view of how the many different puzzle pieces of an organization’s controls come together—or don’t.
The benefit of a holistic strategy may seem obvious, but many businesses compartmentalize data security issues and unknowingly play right into the hands of dishonest employees, warn experts. At the heart of the problem is the tendency of businesses to exclusively focus security efforts on their primary risk. Consumer-facing companies like retailers and others that fall under privacy protection laws often do a better job of auditing their handling of private information, but they may neglect to protect their business secrets.
By leaving it to each department to protect the information they deem it necessary to protect, blind spots often develop, experts warn. Instead, an organization might benefit from an enterprise approach, one that starts with an internal audit to identify all the information it needs to protect. Such an endeavor is best done by a comprehensive cross-functional team or data security task force with members that might include: operational employees with knowledge of the company’s technical and trade secret information; marketing employees with knowledge of the consumer information maintained by the company; human resources employees who know what private information, including protected health information, the company maintains about employees; security or facility managers who understand the company’s physical security; IT personnel who have knowledge of how to secure the company’s computer and technology resources; and legal advisors who can articulate the requirements that apply to the company.
Armed with a full accounting of what needs protection, an insider threat team can analyze the risks insiders pose to it, the controls in place to protect it, and seek to answer the critical question: can we do more to maximize our ability to prevent insider events without inhibiting innovation and work performance?
Experts warn it can be a rabbit hole: the more deeply security leaders examine the insider threat, the more gaps they are likely to find. But they insist that loss prevention—if it is to be comprehensive and responsive to the assets that need protecting today—must look deeply at many aspects of the insider threat.
Who, When, and Why?

All organizations—regardless of size, industry, or region—must recognize the scale of harm they might experience from an insider attack, warned consultant Tommy Hansen, CPP, Hansen Security Risk Management, in a presentation at the GSX+ security conference. “The frequency of incidents has spiked. It’s truly a global challenge on the rise,” he said.
But too many companies treat insider threat security as purely a hiring issue, said Hansen. “In my experience, when organizations are confronted with questions of how they approach insider risk, ‘background checks’ is their answer,” he said. “This is not to say they’re not effective, but they are not effective against people who enter an organization intent on goodwill only to later reveal themselves as an insider.”
Hansen worked as project manager on the development of an insider threat self-assessment tool for the petroleum industry, which he has since translated and encourages any organization to use and adapt (see sidebar). Its fifty questions intend to push organizations to address the life cycle of insider risk and to broaden their approach to prevention. “There is a clear link between an insider act taking place and exploitable weaknesses in an employer’s protective security and management process,” said Hansen. “The point is that we do not rely on one category of measures, for example technological measures, and instead have a holistic approach to insider risk.”
Most employees join an organization in good faith, but a bad performance review, getting passed over for promotion, or a perceived threat of their employment status can change all that, warned Lina Tsakiris, CPP, director of global corporate security programs at the Canadian Imperial Bank of Commerce, in the 2020 GSX+ presentation, “Insider Threats: Understanding the Threat Landscape.” So, too, can outside stressors, such as loss of income, marital issues, or losing a loved one—all more likely in the current global health crisis.
Tsakiris said that in studies of hundreds of insider cases—from theft and fraud, to network sabotage, to the Fort Hood shooter—the insider displayed some sort of indicator in advance and often even told another employee of their intention to harm the organization. “Insider threat is very much a people problem,” she said. “There is a good chance, in fact almost always, that someone was aware of the intended threat before the event occurred.”
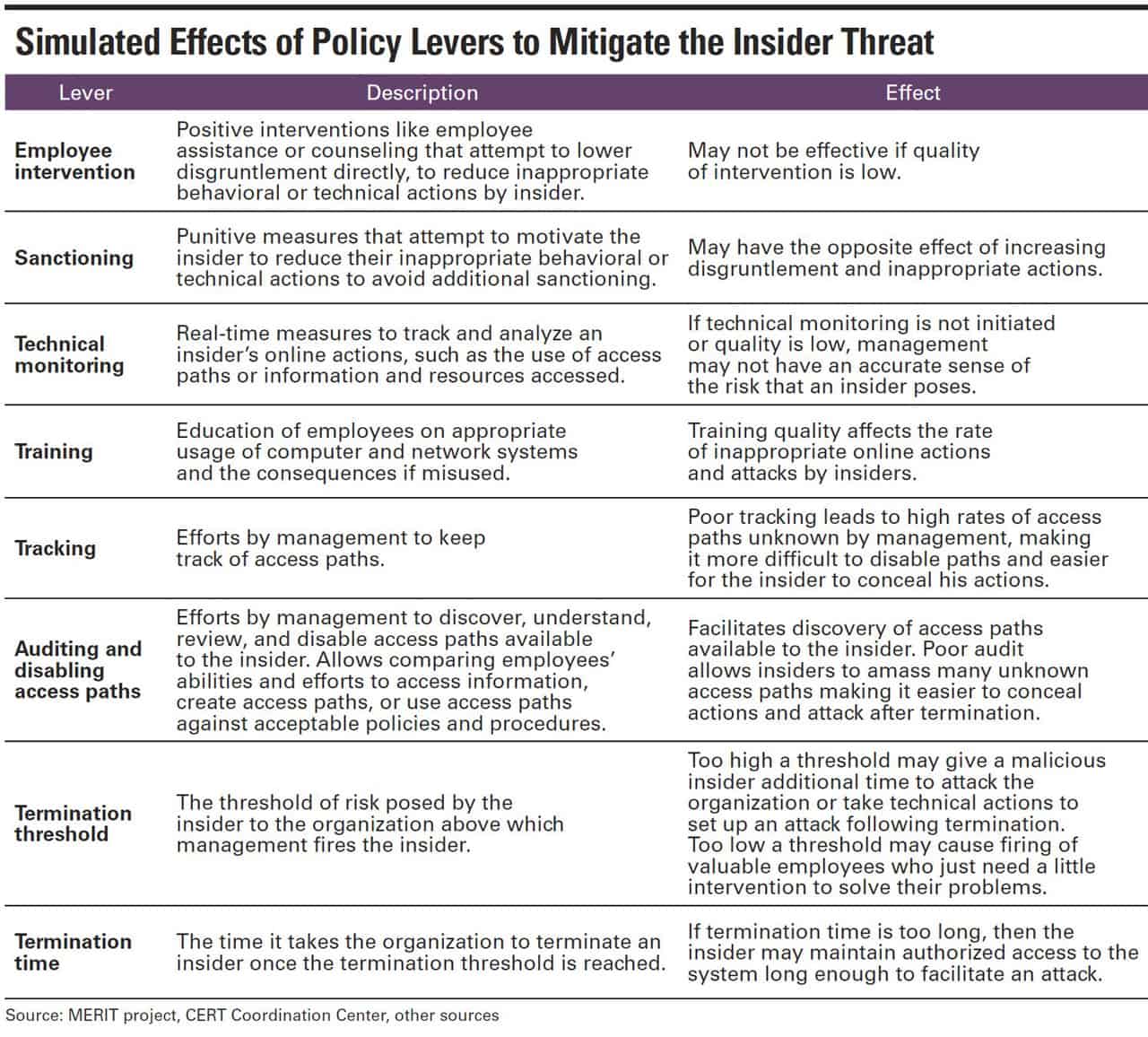
Triggering events can light the spark in cases of insider fraud and are almost certainly behind cases of insider system sabotage or hacking, according to studies by Carnegie Mellon (CM) of insider cases. It finds that “insider disgruntlement contributes directly to the rate of inappropriate technical actions taken by the insider, especially actions that facilitate the attack.”
On a hopeful note, CM’s Management and Education of the Risk of Insider Threat (MERIT) project finds that insiders who hack or sabotage IT systems usually tip their hand that they might do it. In 80 percent of cases, before committing cyber crimes against current or former employers, perpetrators appeared disgruntled, showed up late, argued with coworkers, and/or exhibited other performance problems. In studying sabotage incidents, researchers found worker disgruntlement fell into three familiar categories:
- The insider expected certain technical freedoms using the organization’s computer and network systems but was reprimanded by management for exercising those freedoms.
- The insider expected to have control over the organization’s computer and network system, but control was revoked or never given.
- The insider expected recognition or prestige from management but suffered some sort of rebuke instead, such as being passed over for a promotion.
The issue of rogue behavior among technology systems workers is not abstract. Carnegie Mellon studies of insider cyber-security breaches have found that people in technical positions are the primary culprits, and most of them had system administrator or privileged system access.
In 2018, for example, the FBI’s Las Vegas Division announced it had busted an information technology professional whose job gave him access to the personal information for thousands of employees and customers. He methodically copied that information, took it home, and opened about 8,000 fraudulent and unauthorized PayPal accounts. He then applied for linked credit accounts using the stolen identities and engaged in a series of complex web transactions that ended with him at bank ATMs extracting cash from debit cards. He had eight computers running an automatic script to open online accounts using the names and identifying information he’d stolen from work.
Other data presented at the GSX+ conference suggests that corporations remain preoccupied with staff who, even if dishonest, are generally incapable of doing an organization extensive damage, while often turning a blind eye to workers who can do real harm, such as IT workers. Workers who have access to the purse strings have always presented an obvious insider threat, but in a technology-driven world, it is system operators and specialists who may be able to cause more damage than any single employee could manage to steal.
In addition to being able to cause greater damage, a worker in information systems may not actually deserve the high level of trust they typically enjoy. Some cleaning staff are dishonest, to be sure, but one in three IT employees admit to snooping through confidential information at their workplaces, like wage data and personal emails. Additionally, insider threat research shows it is rare for dishonest workers to go outside of their normal scope of work in the commission of a workplace crime. So while companies should be mindful that unscrupulous cleaning staff might steal someone’s personal property, it should appreciate that the IT department may have an equal percentage of dishonest workers—and that they have far more valuable assets at their disposal. The same company that locks file cabinets to prevent late-night staff from poking where they shouldn’t often gives IT workers the run of the network even when they don’t need it, noted one cyber-security expert.
Organizational change needs to start in the hiring process. Prospective loss prevention and cleaning staff are typically examined with an eye toward “can I trust this guy?” IT workers shouldn’t—but often do—escape the same scrutiny. “Identify where your organization’s risks are. Who in your environment has keys to the kingdom or are in higher risk roles? How capable are they of causing harm to the organization? And then how does that compare to the risk controls in place?” said Tsakiris. “Insider prevention requires good hiring practices and applying life-cycle personnel management to rescreen and conduct enhanced monitoring for employees in higher-risk roles or who are starting to display concerning behaviors,” she added.
Life-Cycle Personnel Management
Knowing that insiders are disgruntled first and strike later, experts focus on the connection between them. Within the gap, they suggest opportunity. If managers, who supervise technical workers and others in unique positions to do harm, recognize performance and behavioral problems as a possible security issue—and communicate it as such—then retail organizations can better prevent incidents.
Several experts advised security leaders to push their organizations to pay greater attention to concerning behavior by an employee following a negative work-related event, to possibly include greater monitoring of the employee’s network activity. A company may not have the capacity to watch everyone’s online activity all the time, in which case it’s valuable to maintain awareness of employee dissatisfaction and troublesome behavior to target proactive system monitoring. Targeted monitoring of online activity by employees of concern can prevent insider theft and sabotage by immediately detecting technical precursor activity, they advise.
The reason behind insider activity is typically complex, according to Hansen. There is often more than one motivation, perhaps a toxic mix of financial troubles, a lack of loyalty, and perceived insufficient recognition. He suggested security needs to be equally layered to match it, by taking a “defense in depth” approach. It starts with looking for indicators of trouble during the hiring process—for financial, personality, and other red flags—but must extend to controls throughout the employee’s lifetime.

One often overlooked risk is when employees temporarily take on roles during job vacancies. Too often, temporary privileges extended to an employee while companies fill positions are never revoked, according to Sherri Ireland, CISSP, president of Security Exclusive, a cyber and physical security consulting firm. “It’s happened to me when I would oversee another department while they were looking for a new hire,” she noted. “It’s really important to audit to make sure your employees have access they require to do their jobs and nothing more than that.” Organizations tend to do a good job advocating for the concept of “least privilege,” but they often do an incomplete job of auditing whether they follow it, she warned.
Security controls also tend to grow lax around long-time employees, which runs counter to the actual threat. “Major employee fraud typically occurs by employees with at least five years tenure,” said Ireland. Case in point: the eye-popping case a decade ago when a Fry’s Electronics employee of twenty years was found guilty of embezzling $66 million over four years. Or the arrest a few years ago of a wireless retailer’s veteran chief operation officer who, for several years, held a secret consulting agreement with a financial services firm to provide it with confidential information regarding sales, compensation, and product launches at the retailer’s 400 locations.
Ireland warned that insider theft is often committed with security controls in mind, citing an example of a retail employee who stole just under its investigation threshold of $50 every day for fifteen years before being caught.

Malique Carr, PhD, a psychologist and vice president for TorchStone Global, a global risk mitigation and security firm, similarly warned that organizations must review their theft prevention posture against both insiders that opt for the “low-and-slow approach and skim a little off the top” and those that go for the big score.
“Employees need privileges to perform their roles effectively and responsibly, but privileges should be accompanied by controls, with segregation of duties for example,” said Hansen. As such, employee monitoring and recognizing threat indicators are key elements in safeguarding a company against the insider threat, along with educating nonsecurity managers about threat indicators. Often, activity a security professional would recognize as a threat, nonsecurity personnel don’t, noted one asset protection professional. “You need cyber-awareness training all the way up to the C-level,” added Ireland.
Once triggered, an insider’s behavior will often reveal their activities if an organization has positioned itself to notice it. Carr said common indicators may include failing to follow security protocols, questionable downloads or data transfers, changes in computer and phone use, and printing off large amounts of material. Data security tools, improved by AI, are a necessary layer of protection against rogue insiders, said Ireland. “IT activity needs to monitor for anomalous activity. Why is she coming in and downloading documents at 3 a.m.?”

Continuous evaluation by technology is hugely valuable, but not as a standalone, according to Scott Stewart, vice president at TorchStone Global. “The AI tools are helpful, but they do require effective and constant analysis from a human being, a human being that is going to look at those records and put their arms around it,” he told the GSX+ audience. “Humans are quite good at spotting insider threat actors. And even better if they are trained. And if there is a good program in place and they know where to report that information, and they know that the information they report is going to be examined professionally and handled confidentially, then insider threat patterns can be disrupted.” Tsakiris made a similar point in her conference presentation: “Awareness of technical and behavior-based indicators that exist is the key to early course correction.”
It’s critical that the life-cycle approach to insider threat security extends to the end of employment, stressed several experts. “If an employee resigns, IT needs to know, and there needs to be monitoring for any unusual activity in the weeks before they leave,” advised Ireland. Some studies suggest that nearly half of insider attacks on company systems are by ex-employees whose access to company systems are not revoked. Disabling access following termination is critical—and to do it effectively, organizations must have full awareness of all access paths available to each of their employees, conference presenters noted.
An access path that is unknown to management is not necessarily illegitimate, but organizations should reduce unknown access paths by identifying them, reviewing each for validity, and disabling those without a justified business need. In investigations of actual incidents, several cases have involved system administrators who created backdoor accounts with system administrator privileges, knowing that because account audits were not conducted the account would not be detected, and they could conduct an attack following the end of employment. Other insiders have configured malicious code logic bombs to go off after getting fired, knowing that their employer didn’t have configuration management procedures to detect it. Finally, other technical insiders used passwords for shared accounts to get in because there was no formal tracking mechanism for access to those accounts, so they were overlooked when the worker was fired. In short, it’s critical that companies don’t perceive removing network access as a procedure to follow when a worker is terminated; rather, as an ongoing process that ensures the performance of proactive, ongoing, rigorous access management practices that make it possible to remove access when a worker is fired.
An insider threat can take many forms: employees, former employees, trusted third‐party suppliers, and contractors and subcontractors. While nefarious motives are certainly behind many insider incidents, Tsakiris said organizations also need to examine how simple mistakes can lead to data leakage, exposure of sensitive materials, or unwittingly cause loss. As the cause of 44 percent of data loss incidents, the unintentional employee insider—either negligent or unwitting—is the single greatest source.
“They are actually the biggest risk,” said Tsakiris. “This is the employee who simply didn’t follow policy and isn’t even aware of what they did.” She said it underscores the importance of building an insider risk program around a holistic approach that includes providing education to workers and creating a workforce culture of security and data protection. “That figure also tells us that we need to be keenly aware of what both malicious and nonmalicious threat indicators look like and to not wait for a threat event to occur for a first point of contact with the insider.”
Mario Paez said retailers should be particularly mindful of the risk from the inadvertent or negligent practices of vendors and suppliers. He cited a case last month when an electronics manufacturer was hit by ransomware, potentially posing a risk to large retail partners, but that they were quick to identify it. “The retailers had some very good vendor risk management and auditing processes in place to react to the incident to make sure their systems were not affected and to assess if their supply chain was going to be impacted,” he said. “Ideally, this is an exposure where retailers should train more eyes and ears. Currently, there is probably not enough attention on that aspect of the insider risk.”
NetSPI’s Florindo Gallicchio agreed, telling LP Magazine that he’s found vendor/employee collusion to be an underrecognized threat by retail organizations. “Shoplifting by customers and employees and underpaying at self-serve checkout lines [are recognized]. Not enough consideration is given to insiders leveraging external/third-party sources to perpetrate a crime,” he said. Risk is present whenever a retailer uses a third-party for generating or supporting their business, he warned. “Retailers must strengthen their procedures and apply accounting checks to every transaction to stop this theft.”
Both Stewart and Hansen stressed the importance of organizational culture in either preventing or promoting insider activity. Security and loss prevention leaders need to be honest about the culture they have if they are to align security controls with the insider threat level. Warning signs accompany insider threat activity, but whether they will be identified, reported, and addressed depends a lot on a retail organization’s existing culture.
“If you develop a good workplace culture, one that cares for people and shows that care, then issues or experiences that might otherwise be triggering events can be a chance to help employees,” said Stewart. “People are more willing to discuss and report issues when there is a sense that the company is interested in helping employees and when it’s not a death sentence for reporting someone’s issues or troubles.” Early intervention not only helps prevent insider threat but also results in greater productivity and employee retention.
“A good security culture is vital, and trust is an important issue,” agreed Hansen, noting that line management plays a particularly important role. “Research indicates that when employees are happy, they thrive. And if they are treated fairly, they are less likely to become insiders. Tell insiders that the organization trusts them but be clear when people join and when rules change that the organization expects them to protect the information and the systems to which they have access. Impress upon them that they have a personal responsibility to uphold the trust and then make trustworthiness concrete for them by describing what are acceptable and unacceptable behaviors.”
Under a New Normal
“During this time of pandemic, major real-world stressors like financial strains from family members losing work, health crises, family deaths, relationship strain leading to breakups, coupled with people not having access to normal coping strategies and support systems, have really created this perfect storm for insiders to act out in ways they wouldn’t normally,” said Dr. Malique Carr.
Experts note that, in some ways, remote work and workforce changes make the insider threat more manageable, in other ways more complicated. A malicious insider may not have the necessary physical access to commit some acts—to an office, or network, or company printer, for example—but they also may be harder to identify as they move through that insider threat kill chain. Regardless, they say, all retail organizations need to review how insider risk may have changed during the pandemic.

The COVID-19 pandemic has brought immeasurable financial, physical, and emotional stress to the world, explains Val LeTellier, an insider risk consultant, former counterintelligence officer, and chair of the Insider Threat Committee on the ASIS International Defense and Intelligence Council. “And make no mistake. Just as ordinary stress levels push insiders to action, extraordinary stress levels push more insiders to greater action.”
In the store environment, the impacts could be profound, thinks Ian Kelly, vice president of operations at NuLeaf Naturals. “I think it is important to remember that employee theft occurs under some specific circumstances: feeling like they are ‘owed’ something and desperation,” he told LP Magazine. “If, as a company, you have been unable to provide enough hours or are cutting corners when it comes to employee support and safety, you will see an increase in employee theft.”
A lack of resources could compound retailers’ troubles. “COVID-19 has certainly changed the nature of the insider threat for retail organizations, and given the reduced workforce retailers are employing, there is reduced monitoring,” warned Gallicchio. Reduced capacity at retail stores to combat attacks could lead to more opportunities for attackers to steal, he suggested.

In the current environment, loss prevention and employee relations are more intertwined than ever, suggests Kelly. “This is a time when employees need to be shown they have value as well as humanity. Doing anything less than this will inspire them to retaliate,” he said. “Even if you are unable to retain all of your employees or give hazard pay, try to give support in other ways.” These include being transparent in communications, extra perks, perhaps steeper employee discounts, and being supportive of employees when they must deal with confrontational customers who put their safety at risk. “You must give employees reasons to be loyal, especially during difficult times when everyone is struggling,” said Kelly.
LeTellier said many companies’ temporary remote work programs are drifting toward permanence. Expect remote work to continue to grow, he said. “With more employees working from home, plus those already working from client sites on the road, the result is an amorphous digital fence, with insiders having greater responsibility but far less direct oversight.”

Alex Sharpe, principal at Sharpe Management Consulting, characterized COVID-19 as the ultimate accelerator for remote work. “Dining room tables became desks. Bedrooms became home offices. Suddenly 42 percent of people were working from home,” he said during his GSX+ presentation, “Securing the Remote Worker and the Cloud.” In-store retail and grocery operations remain familiar, but corporate office models are changing as they are in just about every industry, he said. It complicates conventional insider risk prevention and degrades traditional early warning resources.
“Everything is hybrid, not completely in the cloud and not completely on-premises. The question becomes, then, how do we ensure access control across all applications no matter where the user is located?” said Sharpe. “We’re going to rely more on the remote worker to have good cyber hygiene, and since remote workers very rarely work exclusively from home, usually working in multiple locations and often coming back to the office, we’re going to have to have security processes and policies that transfer across the different environments.”
When the perimeter is porous, identity is critical, as it provides the basis for access control and user permissions. But identity management is all based on a “source of truth,” warned Sharpe. “Who are the employees? Who are the contractors? Are they still employed? What’s the location? What’s the contact information? And then privileges are formed around that. Unfortunately, most sources of truth are out of date,” he said.
Where organizations tend to have a problem, said Sharpe, is failing to update permissions to align with employees as their status and duties change. “A lot of breaches occur because a terminated employee’s account is compromised, and that’s only going to increase.”
Threat indicators are also different for employees of retail organization who are now working from home—many for the first time.
With respect to the unintentional insider risk, there is the potential for sleep issues, greater substance use, or additional stress from multitasking with extra issues at home—and it can be hard to see workers’ level of distraction or disengagement remotely, said Dr. Carr. “This could also be the person who is just not very tech savvy, who might have outdated protection on their home networks, or just someone who is very trusting and open.” Managers should be mindful to watch for an increase in mistakes, late-night emails, alerts that they click on potentially malicious links, oversharing on social media, or poor boundary issues when it comes to work information. “These are employees who now may unwittingly become insiders.”
“Since COVID-19 there has been an explosion in accidental sharing,” according to Sharpe, referring to nonmalicious accidental leaks of company information. As a percentage of information breaches, this has seen a 30 percent increase, he said. “In general, this kind of thing is fairly easy to take care of with awareness training, but as we get into the new normal, it’s something we clearly have to watch.”
The malicious insider risk in work-from-home arrangements is also evolving with COVID, warns TorchStone Global’s Scott Stewart. “It’s easier for employees to fall into insider threat patterns because of stressors, and the two big tools we’ve had to stop it in the past are observation and cohesion. Cohesion leads to loyalty and feelings of responsibility, and that’s been lost in many organizations,” he said, along with less direct observation. Because of fewer “human sensors,” organizations may have to rely more on technical monitoring for insider threat activity.
Training can also help, and many companies have stepped up their training, according to State of Cybersecurity, a study by CompTIA released in September. Along with more advanced technology, and greater use of cyber insurance, they are three ways that organizations are responding to enhanced cyber threats during COVID-19.
Culture Matters
Malique Carr cited a case from May in which a customer service rep was bribed by an external party to provide information on 164 million active users of an online gaming platform. “It was suggested that the worker felt they weren’t being adequately compensated,” she said, noting that such grievances can be harder to pick up on in remote work. The role employees play in systems vulnerability is clear when examining threats by the numbers. Data show 38 percent of system penetrations involve a cooperating insider, Sharpe said. “This number has remained basically stable over the past ten years, roughly two in five.”
Customer service representatives (CSRs) are currently a particular area of concern, said Sharpe: “By the nature of their duties, to resolve customer issues, they need to have more access and capabilities than most system users. And recruitment of CSRs appears to be on the rise. One development that’s been reported anecdotally is that the number of CSRs being approached to sell corporate information has gone through the roof.”
Workers now could be more susceptible to the pitch. Without the peer review from working alongside other employees, natural checks and balances are missing, Sharpe noted. And when it comes to stealing and selling sensitive or proprietary data, the timeline of the insider threat kill chain accelerates when an individual is recruited, warned Stewart.
A recent study by RedOwl and Intsights found front-line retail employees to be frequent targets of sophisticated criminal actors. “Our research showed continued recruiting of retail workers that have access to consumer credit card information,” according to Monetizing the Insider: The Growing Symbiosis of Insiders and the Dark Web.
Employees may be more drawn to commit large insider fraud in the current climate, warns Carr. “Those engaged in insider fraud are likely to have financial stressors, and it may be much easier for someone to engage in fraud if they’re working remotely and don’t feel a sense of attachment and loyalty to a company or their coworkers.” Tip-offs may also be harder to spot, which Carr said may include violations of company financial policy, possible data manipulation, getting a bit too chummy with suppliers, suspicious expenses, or demonstrating excessive control over financial duties. “The insider might also show signs of living large, or larger than you would expect given their position, but when it comes to remote work, you might have to look for more of these signs on social media,” she said.
The malicious ex-worker also demands additional attention in today’s changing work environment. “Especially with remote employees, there needs to be a plan in place to eliminate all access points, retrieve all sensitive data, materials, equipment, and credentials ahead of termination, as it could be really hard to retrieve equipment after the fact,” said Carr.
Sharpe agrees. “Employee termination is the hardest one,” he said. When remote terminations replace those done in-person, traditional catalysts for cutting off credentials are absent. “The moment someone is terminated, shut off everything: their devices, access to applications, their VPN, their MFA. Just have a policy and procedure—automated as much as possible with checks—to terminate it,” he said. “I cannot tell you how many times I have run into situations where something didn’t happen because a termination wasn’t handled personally.” The potential loss from a major incident is substantial, but even minor cases—a terminated employee using a company credit card for months afterward—are still costly.
Even the risk of insider workplace violence may be impacted from today’s world of work. “The remote work environment can be a backdrop to workplace violence, like when delivery personnel use their position to sexually assault a customer, or the recent case in which a man was arrested for a string of interstate shootings while working for a major shipping company,” said Carr.
Compounding the risk from both intentional and unintentional data leakage is that organizations are increasingly making sensitive data available to workers at “end points,” which in the case of a remote worker means their home. Security consultant Alex Sharpe said data show a 41 percent increase in such end-point data since COVID-19, accelerating an existing trend. “With COVID and remote workers, that end point is now outside of our castle. They’re not on our network, and we don’t physically control the space.”
And, often, it means sensitive data resides in insecure devices. Some 90 percent of laptops, for example, are running two versions behind, which include patch levels, according to Sharpe, adding that is the vulnerability through which 60 percent of data breaches occur. “Hackers know that there is now a window, where all the basic blocking and tackling that we have inside the castle is not in place in a remote office, and they try to take advantage of that,” said Sharpe. “They also know that many corporations have spent a lot of time focused on physical and technical controls, but they haven’t instilled a true cyber-security culture, at least not a cyber culture that is appropriate to a home office, so they’re trying to exploit that before that changes.”
Peer pressure tends to reinforce good security practice, and out of view of colleagues, unsafe cyber practices can go unnoticed, Sharpe noted. He said a colleague who runs compliance for a major insurance company said, since COVID-19, that reports to their security hotline went to nearly zero as watchful eyes are removed from the equation. Remote work does make some threats less likely, such as someone exploiting sensitive information they find in a printer, but it changes the threat rather than eliminating it, requiring security to retool to fit.
Sharpe noted that remote work also tends to make workers feel less connected to the enterprise and—because they don’t get that routine feedback natural to in-person environments—are often less secure in their employment prospects. Both are triggers for turning a loyal LP team member or other employee into a potential threat to the organization.
In short, insider threat prevention is getting more complicated. As such, it becomes even more important for organizations to be intentional in getting to know employees, according to Carr. “To be aware of which employees may be more susceptible to becoming an insider, to watch for precipitating events, and to always be screening for possible indicators of insider threat with every online and offline interaction,” she said. “We need to ensure it stays top of mind even while employees are out of sight and to work really hard to create and maintain community and connection.”
Additional Resources
There are many different aspects to the insider threat. The following LP Magazine resources delve deeper into some of them. Each of these articles are linked to the magazine website, LossPreventionMedia.com.
“The ‘Why’ Behind Intellectual Property Theft Cases“
“How to Keep Data Secure from Insider Threats“
“Supply-Chain Security Issues: Reducing the Risk of Data Breach“
In addition, download the PDF “Insider Risk Self-Assessment Tool” available to help security departments benchmark their internal policies and procedures against global standards.
25 Tips for Preventing, Detecting, and Responding to Today’s Insider Threat
Below are quotes compiled from interviews with security consultants, technology officers, LP executives, and expert presenters at the 2020 ISC and GSX+ conferences.
- A governance model is a key foundation of an insider risk program.
- Retailers that segregate systems and are compliant with all required data security and privacy safeguards already greatly reduce insider risk, but you need to be compliant and auditing.
- Use tabletop exercises to examine how your organization would respond to different changes in employee behavior and in a range of different insider threat events.
- Educate senior people about insider threats to prevent an overly “trusting” attitude to flow from the top down.
- To avoid a conflict of interest, incidents captured by an employee hotline or “ethics line” should be accessible by more than one department: HR, legal, security, internal audit, or others.
- Create an insider incident response plan.
- Review controls for time and attendance fraud: it is both exceedingly common and more costly to organizations than most realize.
- Whenever you hire a contractor or consultant, you need to confirm that the individual is not a former employee who was fired for cause.
- Business partner access to computer networks should be accompanied by a formal permission request and an internal business case for why network access is needed.
- Any manager who supervises tech workers that can sabotage company systems should be trained on relevant risk markers, including emotional outbursts, black-and-white thinking, inability to take constructive criticism, and disengagement.
- Social media is an excellent early warning source of potential insider threat activity.
- Insider threat programs can harm morale if operated carelessly. Run all insider threat program activity through a prism of employee privacy and morale issues. Ask, “Does it bring true value to your strategy?”
- Bring a whole-threat approach to an insider threat program.
- Be mindful that money is probably in short supply for company insider risk programs and use that to guide how you advocate for reducing insider threats. A key issue is how you are going to measure and show a return for effort spent to reduce the insider threat.
- Company risk managers are valuable but often underutilized assets for preventing insider threat activity.
- Rotating roles is an excellent practice to ensure redundancy in an organization, improve morale, and deter employee fraud. Separation of duties is an internal business control that helps prevent fraud and identify errors.
- Whether or not you have an established insider threat program, you are probably dealing with insider incidents. It’s important to step back to view how they are being handled and see if there are ways that coordinating the effort might provide efficiencies or reduce risk.
- Including security in new employee orientations can help build a security culture and foster a culture of trust around security issues that makes insider threat activity less likely.
- Top executives can be unintentional insiders. By posting pictures of a family vacation in Spain on Instagram, for example, they create opportunities for spoofing attacks.
- Training the team that is going to be doing an internal investigation is critical. You want to make sure they understand what the process, procedures, and protocols are and that they don’t do their own thing—not only because privacy and employee relations are on the line in insider investigations, but also to avoid overlooking something or missing part of the process.
- Evaluate contracts for whether they prohibit files to be transferred across unprotected networks/systems, which home/personal systems won’t meet.
- Background checks for store employees need to be particularly rigorous for individuals who are going to have access to critical or sensitive data. Especially at middle market retailers, these checks are frequently too cursory.
- Data breach detection, investigation, and response protocols are critical because too often retail organizations have problems detecting and dissecting breaches. It’s why some surveys report external hacking is the source of most incidents while others say it’s insiders.
- Companies allocate resources to protect customer, medical, and payment card information, as they should, but more emphasis needs to be placed on protecting the intellectual property and data that has intrinsic value. If IP is lost, it can cause long-term competitive harm.
- If the issue is solely data leakage, then IT pros can carry the heavy load. But when motives are more sinister, security leaders need to step in.