Just as the word “e-commerce” has come to refer to a menagerie of different specialized markets, so e-commerce credit card fraud comes in many different guises. As the great pace of retail evolution dictates that retailers’ transaction processes are constantly changing, so the frauds change with them.
In a bid to stand on the top of the heap competitively, retailers are offering as many options to consumers as possible when it comes to ways to buy. You can place an online order at an in-store kiosk to be shipped to your house. You can place an order from your mobile device to be picked up at a local store. You don’t like the color of the new curtains you ordered through the online customer rewards program? You can return them to the nearest brick-and-mortar store to save on shipping.

There are many ways for customers to shop in the modern omni-channel retailing world. But this proliferation of transaction processes can leave behind more and more holes that malicious actors can exploit.
“You have this almost complete melding of digital and physical worlds now, and the primary challenge is keeping pace with that evolution,” said Jerett Sauer, director of loss prevention at Gap Inc. “Awareness of risk has always been a core part of any great LP program, and historically, digital space was outside that sphere of awareness; the focus was on people touching a POS or physical merchandise. Now, awareness of the digital space and its crossovers into physical space is equally if not more important.”
The view of a decade past, in which the digital side of retail was a minor extension of the physical backbone of the stores, is poised to flip-flop, and soon the physical brick-and-mortar storefront may be seen as an important, but subsidiary arm of a retailer’s digital foundation.
The age-old, back-and-forth, cat-and-mouse game of criminals finding a new scheme, defenders patching the security hole, and criminals responding by finding a new way to steal is being continually reflected in the retail battleground. One notable exchange in recent history played out in the years immediately after the UK adopted EMV (Europay, MasterCard, and Visa) in 2005–2006.
EMV, known in the UK as “chip-and-PIN,” is a global standard that strengthens card authentication using a computer chip physically built into the card. Instead of reading card data off the card’s magnetic strip, every time a customer inserts their chip card into an EMV-equipped POS card reader, the chip generates a new, unique transaction code. Since the magnetic strip data remains the same with every use, copying that data by card skimming or stealing it in a hack allows the account to be imprinted on counterfeit cards or reused illegally online. But chip-generated codes are one-time use only—stealing one becomes useless.

For the UK, chip-card deployment was largely successful in reducing domestic face-to-face card fraud, but there was a dramatic rise in foreign fraud using UK-issued cards, as well as card-not-present card fraud. “When the UK went to chip-and-PIN, there was a spike in online fraud,” said Scott Sanford, former director of investigations for Barnes & Noble. “The brick-and-mortar card fraud migrated to the online world.”
On October 1, 2015, the US payment card market made a similar move. On that date, the liability for card-present counterfeit card losses shifted from issuer to merchant, unless the merchant implemented EMV. What this liability shift means is that consumers’ cards now have a chip in them, and most brick-and-mortar merchants process cards by reading these chips instead of the conventional magnetic strips, making in-store card counterfeit fraud much more difficult.
While in-store card fraud may fall significantly, many expected e-commerce credit card fraud to jump in response, as it did in the UK. Their predictions seem to be coming true: in early 2017, Javelin Strategy & Research reported that identity fraud, the majority of which is linked to credit card fraud, rose 16 percent and affected more than 15.4 million individuals. Card-not-present fraud, which indicates illegal activity online or via phone rather than in-person, rose 40 percent.
What Does E-commerce Credit Card Fraud Look Like?
“Compared to the professional shoplifter teams of years past who come to stores and shoplift in groups or do basic grab-and-runs, the types of ORC actors you see today are very sophisticated,” said John Matas, vice president of asset protection and investigations, fraud, and ORC at Macy’s. “These groups have the traditional organized crime hierarchy, and the higher the level within the group, the more insulated an individual is from arrest. These groups are well-organized and highly technical, taking full advantage of all sorts of retail processes designed to enhance our customers’ shopping experience, but in a criminal way.”
For example, the realm of gift cards has its own sub-genres of gift card fraud. Legitimate websites intended to store gift cards on your phone have been used by criminals to launder stolen cards. One group broke the mathematical algorithm used to generate gift card number/PIN combinations, then manufactured actual counterfeit credit cards to use them with.

“Friendly fraud” is another problematic category of fraud. Friendly fraud is when the actual cardholder (or somebody known to the cardholder) makes a legitimate purchase, but then tries to dispute the charge by claiming they never made a purchase or never received the merchandise. These are difficult cases for a merchant to challenge.
But rather than giving a brief overview of every type of fraud out there (there are many), this post explores one variety in-depth: the triangulation scheme. The triangulation scheme was ranked the ninth-most impactful type of fraud in 2012 based on frequency of attack and revenue loss; by 2013, triangulation had jumped to the number-one perceived threat, according to a survey conducted jointly between the Merchant Risk Council and CyberSource.
Like many online frauds, the triangulation scheme starts with obtaining stolen credit card account information. For that, the best place to visit is the Deep Web, the name for those realms of the Internet you can’t get to from a Google search. Some parts of the Deep Web are still a Wild West, free from regulation, and may only be reachable using specialized software that masks users in anonymity.
Anonymity
One consequence of the basic structure of the Internet is the ability to easily maintain anonymity against any but the most dedicated investigator. This quality is responsible for much of the value of the Internet as a communications tool, enabling free expression and promoting unfettered exchange of ideas and information. But anonymity is also one of the most attractive reasons to steal over the Internet rather than in person.
The simplest and most common tool to use for Internet anonymity is a proxy server. When a user connects to a proxy server, all of their  Internet traffic will flow through that server, effectively masking that user’s IP address—their digital identity.
Internet traffic will flow through that server, effectively masking that user’s IP address—their digital identity.
Imagine you want to exchange a package with someone using snail mail. Using a proxy would be like hiring an agent to rewrap your package and put their return address on it instead of yours. Then when they receive anything in the mail for you, they forward it to you. Since one proxy may handle thousands of user requests, it becomes difficult to trace any one data stream back to any one of the proxy’s users. There are many legitimate uses and users of proxies, though generally if a merchant finds multiple fraudulent transactions flowing through a particular proxy server, they will blacklist that server. But this is like throwing down a single sandbag to hold back a river. “There are thousands of proxy sites that open every day,” said Sanford. “So the smart criminals are constantly switching around which ones they use.”
But proxies don’t provide perfect anonymity. There are ways to unmask someone behind a proxy. Subpoenas can order a proxy to reveal the user’s IP address, or users may inadvertently let information through the proxy that could be used to localize them. For the ultimate in Internet anonymity, TOR (The Onion Routing) is the answer.
TOR is a software package based on onion-routing software developed in the mid-1990s by the United States Naval Research Laboratory and the Defense Advanced Research Projects Agency (DARPA). The onion analogy refers to the fact that a data exchange made through TOR is wrapped in several layers of encryption and bounced between several nodes. TOR rewraps the data packet like the proxy server did, but then sends the relabeled packet to another proxy, which wraps it in another layer, encrypts it, relabels it, and sends it to a third proxy, which wraps it up, encrypts it, relabels it, and sends it to a fourth party…until after being bounced around several more times, the contents are highly secure and nearly perfectly anonymous. This makes TOR a desirable medium for journalists, law enforcement, militaries, dissidents in countries with draconian communications laws, and, of course, criminals. The first step in many cyber crimes—acquiring stolen credit card information—usually uses TOR.
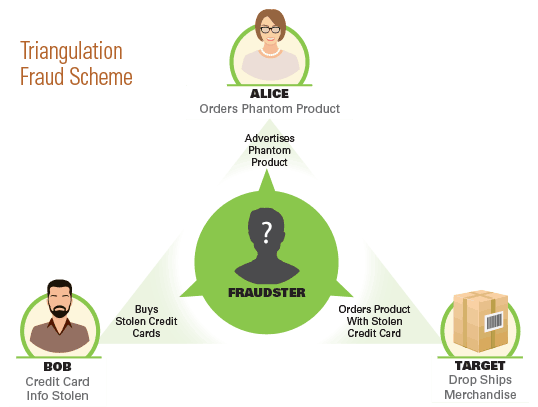
Triangulation Fraud Schemes
So our fraudster—we’ll call him Chuck—has gone to the dark web and bought a few thousand complete credit card account records, including cardholder name, billing address, credit card number, CVV security code, and possibly corresponding email addresses, phone numbers, and other personal information.
The next step in the fraud is listing an item for sale on an online marketplace, such as Amazon, Craigslist, eBay, or any of the thousands of other online auction houses and marketplaces. Nearly any category of merchandise will do—books, clothing, or electronics—as long as the product is in high demand. Chuck decides to list a brand-name laptop for sale. In order to quickly find a buyer, he has to list that laptop at a price point below that of the legitimate sellers out there—if he didn’t, customers wouldn’t have any reason to buy from him over any big-name retailer. The laptop retails at $350, so Chuck (connected through a proxy) posts a listing on eBay for a brand-new laptop for $325 plus free shipping.
Alice is shopping for a laptop. She’s a crafty consumer. She wants to save money. So instead of buying at full retail price, she shops around. She searches eBay, sorts the results by lowest price, and there is Chuck’s listing right at the top. “Wow, what a deal,” she thinks. Alice buys the laptop, and money is transferred from her credit card to Chuck’s PayPal account. Chuck has never been in possession of the laptop. But he can’t just ship nothing to Alice because she would leave negative feedback, file a complaint, and Chuck would find his eBay and PayPal accounts banned. So he has to send her the item she bought. In fact, he wants to appear not only as legitimate, but also as a high-quality, customer-satisfaction-focused seller.
So he goes to his list of stolen credit card accounts and pulls the first one on the list, which belongs to Bob, the legitimate account holder. Using a proxy server, Chuck visits Target’s online storefront to buy the laptop. He uses Bob’s credit card number and billing address, but enters Alice’s shipping address. And then he submits the fraudulent order. Target processes the order and ships Alice the laptop.
Bob is the first victim—he had a fraudulent purchase made on his card. Target is the second victim—it will be hit with a chargeback. And Alice is the third victim—her name and address are on the fraudulent shipment. Thus the triangulation scheme came to be named for these three victims.
Chuck will use Bob’s account only once or twice, and then he’ll drop it and move on to one of the other thousand he has on hand. Target is looking at a $150 loss, so it doesn’t make sense for its team to investigate it. Law enforcement, on top of looking at such a small loss, can’t figure out who Chuck is since he’s been using a proxy server. Both Target and law enforcement might dismiss the whole affair as a minor crime, but Chuck is doing this 10 times a day with 10 different retailers, on each of four different eBay accounts. In reality, there is large-scale fraud going on, but the online medium obscures the fact.
Combating the Triangulation Scheme
Of course, retailers have sophisticated ways to detect fraudulent orders. There are many red flags that could hint that an order is fraudulent, but these are almost never definitive—they merely add some probability that the transaction in question is suspect.
One way that many merchants and third-party fraud prevention vendors combat fraud is by putting every online order through a screening algorithm to look for these red flags and determine how likely it is that an order is fraudulent. These algorithms will frequently have hundreds of very specific criteria they check for. If the order fails one of the checks, the order is flagged with a certain number of fraud alert points commensurate with the likelihood of that criterion being associated with e-commerce credit card fraud. If the order passes a certain point threshold—say 1,000 points—it is sent to an analyst for manual review.
There are the obvious checks: is the shipping address different from the billing address? If so, add 200 points. Is this the first time this card has been used on the site? If so, add 50 points.
Then there are less obvious checks: are the first and last names capitalized? If not, add 200 points. (Apparently, many criminals habitually enter names in all lowercase.) Did the transaction occur late at night? If so, add 50 points.
Then there are more subtle checks: is the transaction placed from a browser configured for a language from a high-fraud country? If so, add 100 points. Does the order originate from a proxy’s IP address? If so, add 400 points. Is the proxy’s IP address out-of-country? If so, add 200 more points.
Another e-commerce credit card fraud test is called “device fingerprinting.” When you visit any website, various bits of information about your computer are shared, such as time zone and type and version of browser and operating system. This information can be analyzed to “fingerprint” an individual device. So if a fraudster is placing multiple fraudulent orders from behind multiple proxies to avoid detection, device fingerprinting can tie together several suspicious orders to reveal that they all came from the same machine.
“Order velocity” is a metric that can be used in a similar way—velocity measures how often the same card is used to place orders on a site. Depending on the item and the merchant’s customers’ normal buying habits, multiple purchases in a short time frame can also point toward fraud.
If an order passes the 1,000-point alert mark, or fails any of the other tests, it gets marked as “suspect” and kicked to a human fraud analyst for review. Analysts have a number of tools at their disposal to help determine whether they should cancel the order or let it go through. They may pay for a public records search to validate order data. They may check social media sites or Google Maps. But they’ll often just call or email the contact information given when the order was placed.
Balancing the Customer Experience
But fraud prevention is a careful balancing act. Weighting too heavily on the side of fraud prevention can negatively impact the customer experience. Asking customers to provide extra information at checkout for validation purposes will at best slow down the transaction, and if done improperly could make customers uncomfortable. And while contacting a customer to verify a purchase might be a positive to some (“this merchant cares about my security”), it could be a negative to others (“this call reduces the convenience of shopping online”).

The last thing a retailer wants to do is drive away legitimate customers who were trying to make a purchase. “There are a lot of merchants out there,” said Tim Guastaferro, director of loss prevention e-commerce and payment systems for Sears, “so if you take steps that make it anything but a seamless transaction, you run the risk of driving that customer to other sites where they don’t have to jump through hoops. It’s not all about fraud losses. We have to balance fraud losses with our customer experience, our operational expense, the ability to take on more payments, to offer more fulfillment types. We want to beat everyone to the scene on implementing these things because they are about enhancing the customer experience.”
“There are tools out there that you can layer on your existing e-commerce platform to drastically reduce the chance of fraud. We could nearly eliminate it,” said Sauer from Gap Inc. “That’s not the issue. The issue is that you would highly impact your customer experience. The balance in how you are trying to structure your program becomes key. You want to make it seamless to 99.9 percent of legitimate customers, but make it just hard enough for fraudsters that they decide to go elsewhere.”
Looking forward, a middle ground might be found in an access control concept called two-factor authentication. ATM withdrawals use two-factor authentication. They require something that a user physically possesses—the debit card—as well as something that a user knows—the PIN.
For card-not-present transactions, the first factor—what they have—would be entered as it is now, manually typing card account information. The second factor—what they know—could be integrated by sending a text message to the mobile device number on file at the card-issuing bank. Since most people keep their phones on them most of the time, confirming a legitimate purchase using a phone could become an accepted non-intrusive step in making an online purchase that could dramatically reduce e-commerce credit card fraud. Retailers, or retailer associations, cannot implement two-factor authentication unilaterally. It requires buy-in on the part of card companies and issuers. But some expect this option to be regarded highly by the payment card industry in the near future.
Investigation
The role of the e-commerce credit card fraud analyst is inherently defensive. Analysts manually review orders that a merchant’s automated fraud prevention system deems suspect. “Analysts can stop an order in its tracks, recall it, or allow it to go through,” said Sanford. “But stopping the order doesn’t dissuade the bad actor. They simply move on to the next retailer or card number, modifying their approach to fly under the radar next time. One thing is certain—unless they’re caught, the online fraudster will continue their efforts one transaction at a time, one credit card number at a time.”
But it is possible to track down these people, and that’s where the investigator comes in. “It starts with the will to find them,” said Sanford, “And it requires a collaborative effort on the part of many players, including online resale venues, banks, ISPs, law enforcement, and sometimes others.” eBay has set the gold standard for this collaborative effort, according to Sanford. “Every major player engaged in peer-to-peer selling could learn something from eBay. They clearly want nothing to do with criminals engaging others on their site,” he said.
One way for a retailer to track down fraudulent sellers is to search online marketplaces for products listed as new but offered at a price below what the retailer is paying for the product. One instance could be a fluke, but if a seller’s sales history shows a pattern of similar offerings, the investigator has most likely found a fraudster. How they proceed from there depends on which marketplace the item is listed under.
Law enforcement won’t look at a case unless it’s a proven fraud event. Investigators can collect a great deal of evidence, but in order to get the final proof and identity information, they need information from the online marketplace. “My team and I have successfully conducted hundreds of investigations over the years,” said Sanford. “Many of these investigations were concluded in partnership with eBay’s PROACT team. Though we’ve also closed numerous investigations involving nefarious Amazon sellers, we’ve taken that trip solo, not by choice either. On the contrary, at least eBay has the decency to respond and show concern for society as a whole. They recognize that we all lose out when the criminal wins.”
Working Together
Taking down cyber criminals is more difficult than just piercing the veil of anonymity to track down who the perpetrator is and where they can be found. “Prosecuting has always been a challenge,” said Sauer. “Early in my career, it was almost impossible since you were usually looking at different parts of the crime being committed in different jurisdictions.” Where a package was shipped from, where it was shipped to, the address of the merchant, the address of the stolen credit card’s legitimate owner—these locations may be in entirely different states, or even different countries. And that’s not even considering the location details of the criminal (or criminals). When considering a fraud scheme that has moved hundreds or thousands of items, each one with multiple different location components, the number of jurisdictions involved can multiply to a staggering number.
Retailers have sophisticated ways to detect fraudulent orders. There are many red flags that could hint that an order is fraudulent, but these are rarely definitive—they merely add some probability that the transaction is suspect.
And the magnitude of loss is often concealed by using multiple accounts and targeting multiple merchants. “If I’m looking at $100 or $1,000 loss from one particular incident,” said Sauer, “even if I know exactly who the perpetrator is, it’s not worth my time or the authorities’ time to prosecute, even if I’ve been hit multiple times. Most cases don’t go above low double-digit thousands as far as loss.” But if a criminal has hit a dozen other merchants in a similar way and has committed the same frauds using several other accounts to minimize his risk, one merchant’s perspective may be just one piece of a much, much larger puzzle.
“If I get hit one night,” said Sears’ Guastaferro, “there’s a good chance that another retailer has been too. So if I communicate with another retailer and they say, ‘We know those people; we know that MO,’ it does make it easier since we can put together a larger case.”
The value of collaboration with other retailers has led to the formation of organizations for that very purpose. “We depend heavily on these organizations for networking and sharing of common ORC offenders,” said Matas. “The most effective are the regional ORCA organizations. There are over twenty-two of these regional coalitions nationwide. Since the ORC and e-commerce credit card fraud phenomenon has spread far beyond the local criminal groups—there are national and international linkages—the next logical step is tying these regional ORCA coalitions into one master national association and creating a unified national ORC database. Together, our ongoing ORC investigations and prosecution dollar value could be significantly larger when it comes to federal prosecution.”
As our digital lifestyles become further intertwined with the physical world, it becomes increasingly important for us to remain aware of the benefits this marriage brings and vigilant of its risks. The complexity of modern digital systems is staggering and continually increasing, making it more and more difficult for any one individual to be able to truly understand how all the pieces fit together. Since increasing system complexity is associated with an increase in the number of possible failure points in the system, total risk exposure increases unless we remain proactive. E-commerce credit card fraud affects individuals just as it does companies and the greater industry, and just as the industry and the company are collaborating and evolving to combat these modern threats, so must we as individuals.
This article was originally published in 2015 and was updated February 28, 2018.


