With online shopping surging 30 percent in 2020, it’s little surprise that cyberattacks are common, with nearly 400 million customer records exposed in attacks on retailers last year, according to calculations by Bloomberg. Such events can do lasting damage—78 percent of customers indicate they would be concerned about doing business with a retailer if the company experienced a breach, according to survey findings released in November by Generali Global Assistance.
Retailers are implementing advanced security to prevent online intrusions, but as retailers expand their online operations, the sheer expanse of their attack surface makes protection difficult. Many experts point to retailers’ desire to create better user experiences—faster shopping, more personalization—as a primary challenge for retailers moving forward. To create fast and easy shopping experience for consumers, retailers must deploy a complex web of applications. And, with more applications at work, the harder it is to spot and manage vulnerabilities.
Successful web application attacks pose a serious threat, accounting for 43 percent of all data breaches in 2019 and up double from the year before, according to the 2020 Data Breach Investigations Report (DBIR) by Verizon. Retail industry data tells a similar story, with web applications becoming the primary target of attacks on the retail industry. “Over the last few years (2014 to 2019), attacks have made the swing away from Point-of-Sale devices and controllers, and toward Web Applications,” according to the DBIR.
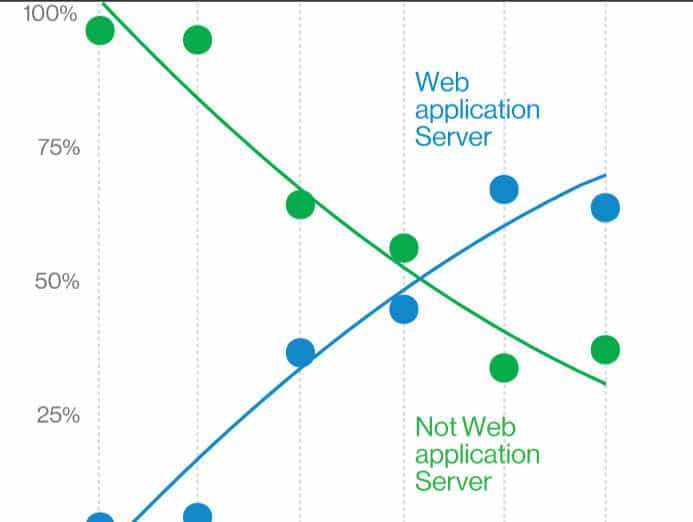
Many web applications contain a labyrinth of layers, according to Stephane Konarkowski, senior security consultant for Outpost24, a provider of vulnerability management technology. “If not designed with security in mind, they can be a breeding ground for vulnerabilities,” he wrote for RSA Conference.
In its research, Outpost24 found 3,357 publicly-exposed web applications running over 401 domains among the top retailers, with eight percent of them considered suspect—often test environments left online and potentially providing a backdoor for bad actors—and 22 percent running on old components.
Exploitation of vulnerable web app infrastructure is one variety of the attack pattern, according to the Verizon DBIR—and the use of stolen credentials is another. Data show the two “are close competitors for first place in the hacking varieties category, and there is not a great deal to distinguish between them from a percentage point of view,” said the report. “In a perfect world, someone else’s data breach would not raise the risk to your own. However, that is increasingly not the case, with the adversaries amassing datastores of credentials from other people’s misfortune and trying them out against new victims.”
Other studies and surveys point to three other strategies that may help retailers get a better handle on current and emerging cyberthreats.
Cybercriminals shift from attacking people to business, requiring a focus on employee behavior. Nationally, data breaches were down 30 percent in 2020, with the number of individuals impacted down more than 60 percent, according to preliminary data from the Identity Theft Resource Center (ITRC). Rather than going away, the ITRC sees a fundamental change in how identity crimes are being committed. Cybercriminals are making more money defrauding businesses with ransomware attacks and phishing schemes that rely on poor human behaviors than traditional data breaches that rely on stealing people’s personal information, according to ITRC predictions for 2021, which it believes could be a long-term trend.
“There is a clear shift in tactics away from cyberattacks that require mass amounts of consumer information to fuel identity crimes—and that’s good news for consumers,” said Eva Casey Velasquez, ITRC president and CEO. “With that said, businesses of all sizes are now the targets of cybercriminals who know how to take advantage of human behaviors—not hope for a technology failure—to rake in billions of dollars.”
Cybercriminals are focusing on cyberattacks that require logins and passwords to get access to corporate networks for ransomware or Business Email Compromise (BEC) scams, according to the ITRC. These attacks require less effort, are largely automated, the risk of getting caught is less, and the payouts are much higher than taking over an individuals’ account, the group notes. Data indicate that the average ransomware payouts for all businesses have grown from less than $10,000 in Q3 2018 to more than $178,000 per event by the end of Q2 2020. “Large enterprises are making average ransomware payments of over $1 million,” said the ITRC 2021 predictions report. “BEC scams cost businesses more than $1.8 billion in 2019.”
Cyber-alignment is worth reviewing. Surveys with information security professionals show that sophisticated, targeted attacks are often the greatest concern and threat to US businesses, but that company IT security teams spend most of their time fixing security vulnerabilities introduced by their own application development teams. Social engineering attacks are similarly shortchanged in time and budget, surveys suggest.
In short, many organizations—and perhaps most—are not spending their time, budget, and staffing resources on the problems that its security-savvy professionals consider to be the greatest threats. While issues such as compliance and application security take a significant amount of their time, cybersecurity teams may need to focus more on emerging threats such as targeted attacks and social engineering exploits. Advice: Retailers should ensure that they’re correctly aiming cybersecurity resources at their greatest risks.
“Executive protection” should have a broader meaning. Because it’s getting harder to get average workers to open unknown email attachments, hackers have been targeting bigger game with more sophisticated weapons. Hackers send extremely specific emails—containing attachments with malicious code to facilitate keystroke recording—to CEOs, including to their personal email accounts, called “whaling.”
The emails differ from mass attacks and are carefully and specifically crafted to encourage the big cheese to open them. Common targets are chief investment officers, company CEOs and presidents, directors of research and development, and chief information and technology officers.
Protecting executives from this threat should include security for family members, as executives’ loved ones have also received targeted email attacks. Tricking a relative into installing malicious code could allow a hacker to obtain sensitive information if an executive uses a home computer for work purposes.
A study by Verizon Enterprise Solutions showed that many high-level individuals with access to privileged information—CFOs, directors of HR, board members, and so on—have increasingly become the specific targets of hackers as they focus their aim. In the past, attackers used “spray-and-pray” tactics where they would attack broadly and hope to hit something. Targeting is now more refined, the study showed. More and more, studies find that malware samples are unique to a specific organization.
When an attack is highly targeted and customized to a particular organization, it becomes harder to identify and can be difficult to recognize as something suspicious, warned Ed Powers, partner and former managing principal for Cyber Risk Services at Deloitte & Touche. His advice: Assume that some of these attacks are going to be successful to some degree, and plan accordingly. That is, be prepared to react quickly and effectively to minimize the business impact of successful hacks.